The exponential growth of mobility poses new management obstacles for your data center. The increasing array of mobile devices, users, and wireless networks has broadened to a business context--affecting how most companies operate today. Managing mobile factors like deploying apps and setting guidelines for BYOD (Bring Your Own Device) are essential for growing with mobility. Organizations must grow mobile connections with users and customers, understand the importance of mobile integration, and determine solutions to fulfill business needs.
Mobility in Action

The time of video calls, web conferencing, and instant access is now. Mobility allows users to access information from any country on any network through voice over Wi-Fi, voice over 3G/4G, or cellular. Privacy concerns arise with mobile users when connecting on their devices, but features like “dual persona” maintain separate identities to allow for separation of business and personal communications on a single device. Employees can keep their mobile number private by accessing their desk phone from their cellular, and managers can rest assured that customer lists and information stay with the company, not the employee. This mobile trend will only continue to grow, and businesses must adapt by growing their own mobile connections.
Our leading partners in mobility, HP and ShoreTel, offer these solutions to better equip your organization for the rapid increase of mobile-use in the office. Proper guidelines regarding personal devices are important for proper mobile integration. BYOD refers to the policy of permitting employees to bring personally-owned mobile devices to their workplace, and to use those devices to access privileged company information and applications. Mobile access to business assets poses mobility concerns that organizations must understand to determine appropriate solutions.
Mobility and Security
Security concerns top the list of reasons to implement strict BYOD guidelines. A majority of organizations attribute increased security incidents to mobile devices, also agreeing that careless employees can be a greater security threat than hackers. Employees have access to corporate email and may have business contacts and customer data saved on their mobile device. Ensure your customers’ privacy and keep data secure with policy-driven device management.
Wi-Fi usage and network connection also challenge your data center with the growth of mobility. Your organization must consider scalability and density of the network to support these new devices. Onboarding is also essential to BYOD- identifying user specifications at different levels, whether internal, semi-secure, or guest-user to determine access compliance.
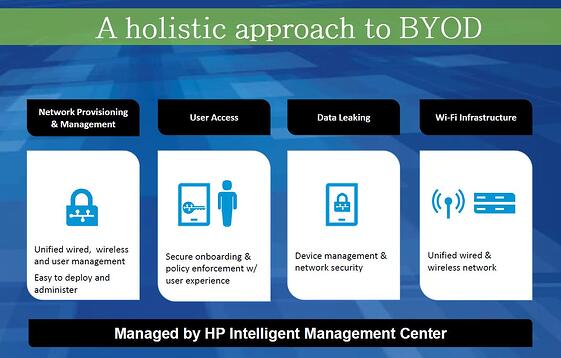
Other BYOD essentials include provisioning and monitoring. Companies must enforce unified policies independent of geography. Policy-based guidelines will keep your network secure of opposing threats and proper solutions will alert your system to appropriate action. These guidelines will be monitored and drive access policies based on user behavior. Obtain a solution that will quarantine devices with any detected threats. Experience more of the growth of mobility by downloading these slides:

